Cahier groupe n°5 : Différence entre versions
De Wiki d'activités IMA
(→Progress) |
(→Session 10 (04/01/2016)) |
||
| (58 révisions intermédiaires par le même utilisateur non affichées) | |||
| Ligne 1 : | Ligne 1 : | ||
== Useful information == | == Useful information == | ||
| − | |||
| + | '''Gabriel Pagola Nielsen''' & '''Jérémie Denéchaud'''<br/> | ||
| + | ; Xen Vitural Machine | ||
| + | : Name - troubadour | ||
| + | : Address - '''193.48.57.165'''<br/> | ||
| + | : | ||
| + | ; WiFi hotspot - Particular task | ||
| + | : Name - Troubadour | ||
| + | : Address (first part) - '''172.26.79.11'''<br/> | ||
| + | : Address (second part) - '''10.10.10.2'''<br/> | ||
| + | : Username/password - Cisco/Cisco | ||
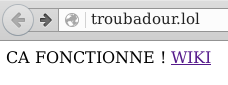
| + | ; Website | ||
| + | : HTTP Address : [http://troubadour.lol/] | ||
| + | : HTTPS Address : [https://troubadour.lol/] | ||
| + | |||
| + | ; Group WiFi hotspot | ||
| + | : Username/password - user/toto | ||
| + | |||
| + | === Progress === | ||
| + | |||
| + | ; <span style="color: green;">Particular task - PART 1 | ||
| + | : Configuration of the wifi AP | ||
| + | : Route through Polytech gateway (172.26.79.254) | ||
| + | : MAC address filtering on half the eeePC | ||
| + | : Tests | ||
| + | ; <span style="color: green;">Particular task PART 2 | ||
| + | : Route through local gateway (10.10.10.254) | ||
| + | : Telnet accessibility | ||
| + | ; <span style="color: green;">Configuration of the xen VM</span> | ||
| + | : Creation & installation of packages | ||
| + | : SSH accessibility | ||
| + | ; <span style="color: green;">Wifi WEP crack </span> | ||
| + | ; <span style="color: green;">Wifi WPA crack </span> | ||
| + | ;<span style="color: green;">DNS - Bind configuration</span> | ||
| + | : Buying troubadour.lol domain name and the certificate | ||
| + | : Bind server, IPv4 and IPv6 configuration | ||
| + | ;<span style="color: green;">SSL Certificate </span> | ||
| + | ;<span style="color: green;">DNSSEC</span> | ||
| + | ;<span style="color: orange;">RAID5</span> | ||
| + | ;<span style="color: red;">Crypted SD card</span> | ||
| + | ;<span style="color: green;">FreeRadius ID server configuration </span> | ||
| + | ;<span style="color: green;">WPA2-EAP-secured wifi network </span> | ||
| + | ;<span style="color: red;">PCBX configuration </span> | ||
== Specification of the specific task == | == Specification of the specific task == | ||
| Ligne 10 : | Ligne 51 : | ||
We use a Cisco Aironet 2600 wifi access point. | We use a Cisco Aironet 2600 wifi access point. | ||
[[Image:Product image large.jpg|thumb|Cisco Aironet 2600 access point]] | [[Image:Product image large.jpg|thumb|Cisco Aironet 2600 access point]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Progress monitoring == | == Progress monitoring == | ||
| − | === | + | === Session 1 (01/10/2015) === |
Steps to follow : | Steps to follow : | ||
* Connecting via serial link to the Cisco Aironet 2600 | * Connecting via serial link to the Cisco Aironet 2600 | ||
| Ligne 33 : | Ligne 59 : | ||
* Accessing the hotspot via ethernet | * Accessing the hotspot via ethernet | ||
* Using the web interface to configure mac address filtering | * Using the web interface to configure mac address filtering | ||
| − | |||
| − | |||
| − | === | + | === Session 2 (08/10/2015) === |
* Configuration of the Wifi AP | * Configuration of the Wifi AP | ||
minicom -os //9600 bauds<br/> | minicom -os //9600 bauds<br/> | ||
| Ligne 49 : | Ligne 73 : | ||
** Unknown problem that lead to the reset of the Access point | ** Unknown problem that lead to the reset of the Access point | ||
| − | === | + | === Session 3 (15/10/2015) === |
* Reset of the Access point | * Reset of the Access point | ||
* Mac address filtering working correctly | * Mac address filtering working correctly | ||
| − | * Creation of | + | * Creation of the AP (SSID = "troubadour") |
* Filtering half of the eeePC | * Filtering half of the eeePC | ||
| + | * Penetration test by MAC spoof from an eeePC : | ||
| + | ifconfig wlan0 hw ether XX:XX:XX:XX:XX:XX | ||
| − | === | + | === Session 4 (22/10/2015) === |
| + | * Creation of the virtual drives | ||
* Configuration of the xen virtual machine "troubadour" | * Configuration of the xen virtual machine "troubadour" | ||
xen-create-image --hostname=troubadour --ip=193.48.57.165 --netmask=255.255.255.240 --gateway=193.48.57.174 --dir=/usr/local/xen | xen-create-image --hostname=troubadour --ip=193.48.57.165 --netmask=255.255.255.240 --gateway=193.48.57.174 --dir=/usr/local/xen | ||
--mirror=http://debian.polytech-lille.fr/debian/ --dist=jessie --passwd | --mirror=http://debian.polytech-lille.fr/debian/ --dist=jessie --passwd | ||
| + | |||
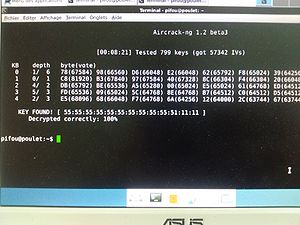
| + | === Session 5 (12/11/2015) === | ||
| + | * Successful wifi WEP encryption crack | ||
| + | * SSH accessibility of the VM. | ||
| + | [[Fichier:crack_wep_denech.jpg|center|thumb|300px|WEP Encryption crack]] | ||
| + | |||
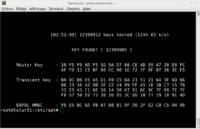
| + | === Session 6 (19/11/2015) === | ||
| + | * Wifi WPA encryption crack attempt almost successful | ||
| + | * Cap file & handshake captured | ||
| + | * dictionnary created with the powerful command '''crunch''': | ||
| + | crunch 8 8 -o wl.txt -t %%%%%%%% | ||
| + | * Problems with apt-get to download aircrack on tutur | ||
| + | <br /><br /> | ||
| + | |||
| + | === Session 7 (25/11/2015) === | ||
| + | [[Fichier:crack_wpa_denechaud.png|200px|thumb|right|Crack of the WPA key]] | ||
| + | * Aircrack of the previously captured cap file | ||
| + | * Successful WPA crack | ||
| + | * Configuration of the wifi hotspot for the local network | ||
| + | ip default-gateway 10.10.10.254 | ||
| + | * Telnet accessibility from a VM | ||
| + | * Configuration of the DNS server following [https://wiki.gandi.net/fr/hosting/using-linux/tutorials/debian/bind this tutorial] | ||
| + | * Beginning of SSL configuration while Gandi processes the DNS change | ||
| + | [[Fichier:dns2_denech.png|100px|thumb|DNS analyse by digicert.com]] | ||
| + | * Successful DNS configuration : | ||
| + | <br /> | ||
| + | [[Fichier:dns_denech.png|Bind is correctly feeding the domain name]] | ||
| + | <br /><br /> | ||
| + | <br /><br /> | ||
| + | |||
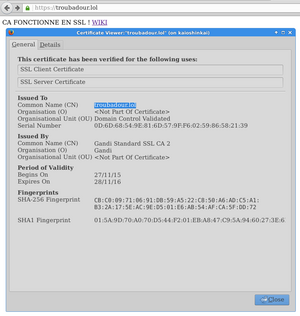
| + | === Session 8 (26/11/2015) === | ||
| + | * End of SSL certification following [https://wiki.gandi.net/fr/hosting/using-linux/tutorials/ubuntu/ssl this tutorial] | ||
| + | * Fixing a conflict in /etc/apache2/ports.conf | ||
| + | ** Apache2 would not restart because of an already-listened-to 443 port | ||
| + | ** The port 443 was listened by a previous module | ||
| + | ** All other modules listenning to 443 port were commented out | ||
| + | * Successful SSL configuration for www.troubadour.lol and troubadour.lol | ||
| + | |||
| + | [[Fichier:ssl2_denech.png|thumb|300px|center|Firefox is happy, the connexion is secured]] | ||
| + | |||
| + | * Fixing a bug on the IPv6 address, causing the DNSSEC to fail | ||
| + | ** TCP and UDP transit didn't seem to work | ||
| + | ** Port 53 seemed closed (according to [https://www.zonemaster.fr/test/9b93b0fe724c9298 zonemaster.com]) | ||
| + | ** A correct rebuild of Bind worked | ||
| + | |||
| + | [[Fichier:dnssec_denech.png|thumb|300px|center|Results on the different test of zonemaster.com]] | ||
| + | <br/><br/> | ||
| + | |||
| + | === Session 9 (03/12/2015) === | ||
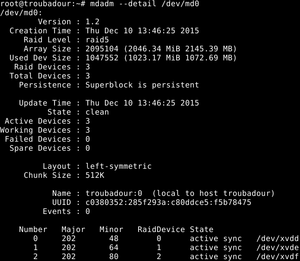
| + | [[Fichier:raid5_denech.png|thumb|right|RAID5 configuration]] | ||
| + | * Configuration of the Radius server | ||
| + | ** New client, VLAN and user | ||
| + | ** PEAP encryption instead of MD5 | ||
| + | * RAID5 configuration | ||
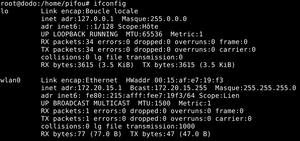
| + | [[Fichier:wifi_denech.png|thumb|left|WiFi interface connected to our hotspot]] | ||
| + | <br/><br/><br/><br/><br/><br/><br/><br/> | ||
| + | === Session 10 (04/01/2016)=== | ||
| + | * Correction of errors on the raid5 drives | ||
| + | ** The drive mount sequence was wrong (Automatic mount of an non-existent raid drive) | ||
| + | ** Removing the mdadm deamon solved the problem | ||
| + | ** Only downside : the raid has to be configured on each reboot | ||
| + | ** Automatic "md127" appears | ||
| + | mdadm --stop /dev/md127 | ||
| + | [ 37.984366] md: md127 stopped. | ||
| + | [ 37.984382] md: unbind<xvdf> | ||
| + | [ 37.984388] md: export_rdev(xvdf) | ||
| + | [ 37.984420] md: unbind<xvdd> | ||
| + | [ 37.984425] md: export_rdev(xvdd) | ||
| + | mdadm: stopped /dev/md127 | ||
| + | * This commands are mandatory for a correct detection of our raid on md0 | ||
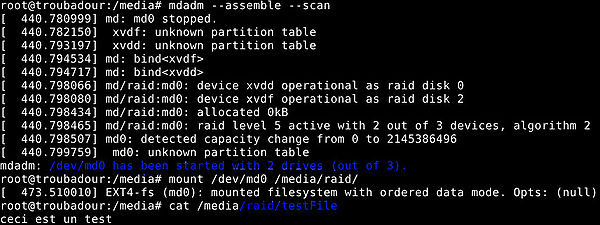
| + | * Test with a file on the raid | ||
| + | ** Even with one disk less (here xvde) we can mount the raid and see its content | ||
| + | |||
| + | [[Fichier:Testraid5_jed.jpg|thumb|600px|center|Successful test of the RAID5 drives]] | ||
Version actuelle datée du 4 janvier 2016 à 16:26
Useful information
Gabriel Pagola Nielsen & Jérémie Denéchaud
- Xen Vitural Machine
- Name - troubadour
- Address - 193.48.57.165
- WiFi hotspot - Particular task
- Name - Troubadour
- Address (first part) - 172.26.79.11
- Address (second part) - 10.10.10.2
- Username/password - Cisco/Cisco
- Group WiFi hotspot
- Username/password - user/toto
Progress
- Particular task - PART 1
- Configuration of the wifi AP
- Route through Polytech gateway (172.26.79.254)
- MAC address filtering on half the eeePC
- Tests
- Particular task PART 2
- Route through local gateway (10.10.10.254)
- Telnet accessibility
- Configuration of the xen VM
- Creation & installation of packages
- SSH accessibility
- Wifi WEP crack
- Wifi WPA crack
- DNS - Bind configuration
- Buying troubadour.lol domain name and the certificate
- Bind server, IPv4 and IPv6 configuration
- SSL Certificate
- DNSSEC
- RAID5
- Crypted SD card
- FreeRadius ID server configuration
- WPA2-EAP-secured wifi network
- PCBX configuration
Specification of the specific task
Presentation of the particular task
The specific task consist in configuring one of the two wifi access point (AP). Those APs are connected to the Cisco Catalyst 6009 switches to provide further redundancy.
Hardware used for the particular task
We use a Cisco Aironet 2600 wifi access point.
Progress monitoring
Session 1 (01/10/2015)
Steps to follow :
- Connecting via serial link to the Cisco Aironet 2600
- Adapting the configuration for insecure network
- Accessing the hotspot via ethernet
- Using the web interface to configure mac address filtering
Session 2 (08/10/2015)
- Configuration of the Wifi AP
minicom -os //9600 bauds
en
config
interface BVI 1
ip address 172.26.79.11 255.255.240.0
end
write
- Using the web interface to configure mac address filtering (root:Cisco)
- Different tests to enable mac filtering
- Unknown problem that lead to the reset of the Access point
Session 3 (15/10/2015)
- Reset of the Access point
- Mac address filtering working correctly
- Creation of the AP (SSID = "troubadour")
- Filtering half of the eeePC
- Penetration test by MAC spoof from an eeePC :
ifconfig wlan0 hw ether XX:XX:XX:XX:XX:XX
Session 4 (22/10/2015)
- Creation of the virtual drives
- Configuration of the xen virtual machine "troubadour"
xen-create-image --hostname=troubadour --ip=193.48.57.165 --netmask=255.255.255.240 --gateway=193.48.57.174 --dir=/usr/local/xen --mirror=http://debian.polytech-lille.fr/debian/ --dist=jessie --passwd
Session 5 (12/11/2015)
- Successful wifi WEP encryption crack
- SSH accessibility of the VM.
Session 6 (19/11/2015)
- Wifi WPA encryption crack attempt almost successful
- Cap file & handshake captured
- dictionnary created with the powerful command crunch:
crunch 8 8 -o wl.txt -t %%%%%%%%
- Problems with apt-get to download aircrack on tutur
Session 7 (25/11/2015)
- Aircrack of the previously captured cap file
- Successful WPA crack
- Configuration of the wifi hotspot for the local network
ip default-gateway 10.10.10.254
- Telnet accessibility from a VM
- Configuration of the DNS server following this tutorial
- Beginning of SSL configuration while Gandi processes the DNS change
- Successful DNS configuration :
Session 8 (26/11/2015)
- End of SSL certification following this tutorial
- Fixing a conflict in /etc/apache2/ports.conf
- Apache2 would not restart because of an already-listened-to 443 port
- The port 443 was listened by a previous module
- All other modules listenning to 443 port were commented out
- Successful SSL configuration for www.troubadour.lol and troubadour.lol
- Fixing a bug on the IPv6 address, causing the DNSSEC to fail
- TCP and UDP transit didn't seem to work
- Port 53 seemed closed (according to zonemaster.com)
- A correct rebuild of Bind worked
Session 9 (03/12/2015)
- Configuration of the Radius server
- New client, VLAN and user
- PEAP encryption instead of MD5
- RAID5 configuration
Session 10 (04/01/2016)
- Correction of errors on the raid5 drives
- The drive mount sequence was wrong (Automatic mount of an non-existent raid drive)
- Removing the mdadm deamon solved the problem
- Only downside : the raid has to be configured on each reboot
- Automatic "md127" appears
mdadm --stop /dev/md127 [ 37.984366] md: md127 stopped. [ 37.984382] md: unbind<xvdf> [ 37.984388] md: export_rdev(xvdf) [ 37.984420] md: unbind<xvdd> [ 37.984425] md: export_rdev(xvdd) mdadm: stopped /dev/md127
- This commands are mandatory for a correct detection of our raid on md0
- Test with a file on the raid
- Even with one disk less (here xvde) we can mount the raid and see its content